The TFM Tool is a powerful asset in a mobile repair technician’s toolkit, but its real value is unlocked through a precise, methodical approach. We know the common frustrations: driver conflicts causing “device not detected” errors, uncertainty about whether a specific model or security patch is actually supported, and confusion about the credit system. These roadblocks waste time and risk client devices.
This guide is built to solve those exact problems. We provide a conflict-free driver installation procedure with direct links, a realistic guide to chipset and security patch compatibility, and clear risk management protocols for every job. By following these steps, you can avoid common errors and make the TFM Tool a reliable part of your daily workflow.
In This Guide
- Conflict-Free Driver Installation Procedure
- A Realistic Guide to Supported Models
- How to Perform a Pre-Service EFS/NVRAM Backup
- TFM Tool vs. Chimera vs. UnlockTool: A Business Comparison
- Understanding TFM Tool Credits and Activation
- Frequently Asked Questions for Technicians
TFM Tool Download and Setup: A Conflict-Free Driver Procedure
The most common point of failure is incorrect driver installation. This issue almost always stems from conflicts with existing drivers. To prevent this, you must follow a standard operating procedure for a clean installation.
The Driver Installation and Verification Procedure
1. Uninstall Conflicting Drivers: Before you begin, navigate to Windows “Apps & features” and uninstall any existing mobile device driver packages. This includes official OEM software like Samsung Smart Switch or Mi PC Suite, and any drivers left over from other service tools. A clean slate is essential.
2. Download Official Software: Get the latest version of the TFM Tool software and the required driver pack directly from the official source. Using official installers prevents issues with outdated or modified files.
- Official TFM Tool Software: Download from the Official TFM Tool Website
- Official TFM Tool USB Driver Pack: Download the TFM Driver Pack
3. Install Prerequisites: Install any necessary Smart Card drivers (for physical boxes) and required runtime libraries like Microsoft Visual C++ Redistributables.
4. Disable Driver Signature Enforcement (Windows 10/11): This is a critical step, not an optional one.
- Go to Settings > Recovery > Advanced startup and click Restart now.
- On the blue screen, select Troubleshoot > Advanced options > Startup Settings and click Restart.
- After the reboot, press 7 or F7 on your keyboard to select Disable driver signature enforcement.
5. Install the Official USB Driver Pack: With signature enforcement disabled, run the installer for the TFM Tool USB drivers.
6. Reboot Your Computer: A full system reboot is non-negotiable to load the new driver stack.
7. Verify in Device Manager: Connect a device in the appropriate service mode (e.g., MTK BROM or Qualcomm EDL). Open the Windows Device Manager and check for the correctly named hardware under ‘Ports (COM & LPT)’ or ‘Universal Serial Bus controllers’.
TFM Tool Supported Models: A Realistic Chipset and Patch Guide
Success in 2025 depends on the device’s chipset, firmware version, and security patch level. An operation is only possible if the tool has an exploit for a specific binary. Always check the tool’s latest release notes before starting a job.
- MediaTek (MTK): TFM offers robust support via MTK BROM/preloader mode. Success on newer devices often requires bypassing Secure Boot, which may require using test points on the motherboard or a specialized boot cable.
- Qualcomm (Snapdragon): Support relies on forcing the device into Emergency Download Mode (Qualcomm EDL 9008). Accessing EDL on newer models often requires either physical test points or an authorized EDL account for the tool to authenticate with the manufacturer’s servers.
- Samsung (Exynos/Snapdragon): Support is dictated by the bootloader version (binary revision, e.g., U4, S5). An operation that works on one binary version will fail on a newer one. Always verify the full firmware version against the tool’s supported list.
How to Perform a Pre-Service EFS/NVRAM Backup
The single greatest technical risk is corrupting a device’s EFS or NVRAM partitions, which store the IMEI. Wiping them can permanently brick cellular functions. A pre-service backup is your non-negotiable safety net.
The EFS/NVRAM Backup Procedure
1. Connect in Service Mode: Use the appropriate method for the chipset, such as MTK BROM or Qualcomm EDL 9008.
2. Navigate to the Backup Tab: In the TFM Tool software, find the section for backup, service, or readback functions.
3. Select Security Partitions: Check the boxes for EFS, NVRAM, and/or MODEM. When in doubt, back up all security-related partitions.
4. Execute and Save Securely: Start the backup. Save the file and name it with the device’s serial number, model, and date (e.g., SERIAL123_SM-G998U_2025-10-07.bin).
TFM Tool vs. Chimera vs. UnlockTool: A Business-Focused Comparison
Choosing the right tool is a critical business decision. This comparison helps you make an informed investment based on your shop’s service profile.
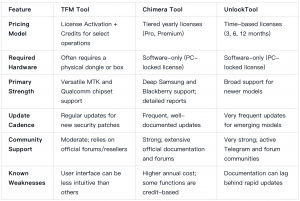
Understanding TFM Tool Credits and Activation
The TFM Tool uses a hybrid model: an initial license activation, plus credits for certain high-level or server-dependent operations.
What Consumes TFM Tool Credits?
- Newer Security FRP Removals: For some recent security patches, the bypass calculation must be done on a secure server, which consumes credits.
- Carrier Unlock Services: Network unlocks almost always require a server-side process and use credits.
- IMEI Repair/Modification: On supported models (and where legally permissible), these are premium, credit-based functions.
To avoid scams, purchase your license/credits only from authorized resellers listed on the official TFM Tool website.
Frequently Asked Questions for Technicians
Is a physical dongle or box always required for TFM Tool?
It depends on the specific TFM product you purchase. Some are software-only activations, while others are tied to a physical dongle or service box for security. Check the product description from the reseller before making a purchase.
How often should I perform an EFS/NVRAM backup?
You should perform a backup before every single operation that writes to the device’s memory, including FRP removal, flashing, and unlocking. It should be a mandatory step in your service checklist.
What’s the biggest risk when using physical test points?
The primary risk is permanent hardware damage. A small slip of the tweezers can short the wrong components on the motherboard, bricking the device. This method should only be used by experienced technicians who accept the risk.
Can TFM Tool fix a “hard-bricked” device that won’t turn on?
If the device can be forced into a low-level service mode like EDL 9008 or BROM, then yes, TFM Tool can potentially revive it by flashing the correct firmware. However, it cannot fix underlying hardware failure.
Conclusion
Mastering the TFM Tool is about adopting a disciplined procedure for every job. By implementing a conflict-free driver workflow, verifying support based on the reality of chipsets and security patches, and always performing critical pre-service EFS backups, you can make it a predictable and profitable asset for your repair business. This methodical approach protects your clients’ devices, manages risk, and builds your shop’s reputation for reliable, expert service.